Network Penetration Testing
Comprehensive penetration steps and methodologies to secure your digital assets effectively.
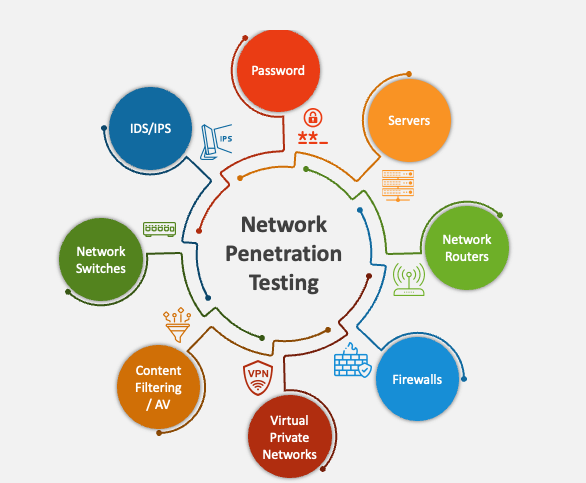
Assessment Methodology Overview
Detailed steps for effective vulnerability assessment and risk management strategies.
Risk Identification Process
Identify potential vulnerabilities and assess their impact on your organization’s security posture.
Mitigation Strategies Overview
Implement effective strategies to mitigate identified vulnerabilities and enhance overall security.
Get in touch
Address
GR Samriddhi, No.273, 1st Floor, 7th Cross, Basavanapura Main Rd, near Silicon City College, Krishnarajapuram, Bengaluru, Karnataka – 560036.
Contact
Mobile : +91 99647 22968
Email : info@cypros.in





